Vpcs
Table of Contents
1. Subnets
A subnet is said to be public if and only if it a route exists in it's route table to an internet gateway, else a subnet is said to be private. For example:
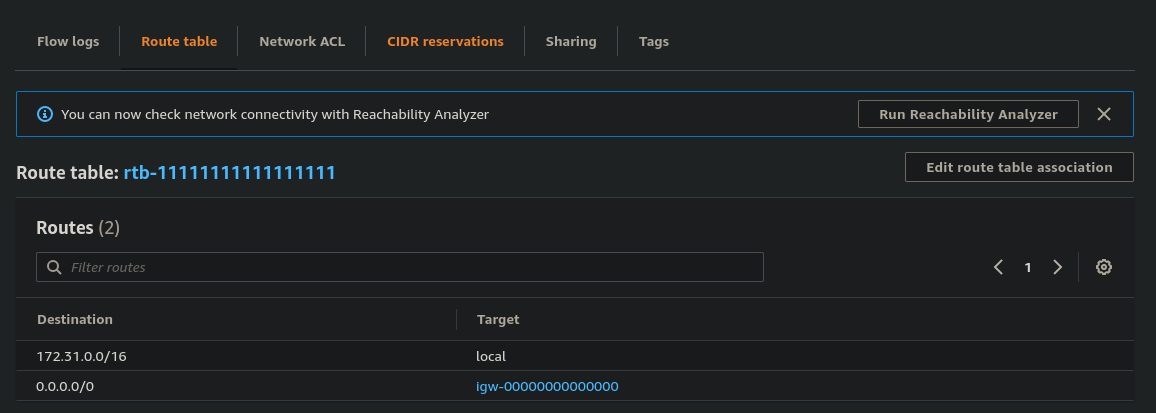
We see the default gateway destination (0.0.0.0/0) is set to an internet gateway, thus the subnet is public.
In a public subnet however, it is also necesarry to assign public ips to instances which need to be accessible from the internet and access the internet. This can be done by enabling the Auto-assign public IPv4 address on the subnet, or alternatively assigning elastic ip addresses.
In order to make instances in private subnets able to access the internet, it's recommended to create a NAT gateway, and an entry for the gateway in each of the private subnet route tables you want to enable outbound traffic for.
1.1. Routing Encore
Also noteworthy is by default all subnets within a VPC can communicate with each other. This is illustrated by the first entry in the image above with Target local, which by default is added to all route tables.
If your route table has multiple routes, the most specific route that matches the traffic (longest prefix match) is used - so in the image above it doesn't matter whether the default root precedes or supersedes the other.
2. DNS
DNS support is determined by the EnableDnsSupport and EnableDnsHostnames VPC attributes. The former (enabled by default) means DNS queries to the local Route 53 Resolver for the applicable AZ succeed on the VPC; the latter means instances with public IPs will be assigned public IP addresses.
Note instances will generally receive a private IP address and private DNS hostname regardless of the VPC attributes, though the EnableDnsHostnames attribute for the VPC will determine if the instance will be assigned a public IP.